
Gay Gordon-Byrne
In February, a newly minted trade association calling themselves the Security Innovation Council (SIC) put out a study about consumer fears over cyber security risk and their perceptions of repair-related risk.
We all know consumers are frightened of losing their bank accounts, personal data, or privacy. So who hired a company to study the obvious?
The answer is immediately clear when one asks “Who benefits from creating more fear?” Answer: Manufacturers that want to continue to monopolize repair. Some manufacturers have been trying to scare consumers into thinking that repair is a real risk to cyber security – in order to drive repair business exclusively to their doors. Even more importantly, some of these same manufacturers who prefer to be the only source of repair are currently fighting “right to repair” legislation to protect their repair monopolies (see related story about the introduction of a right to repair bill in California).
As it happens, the entire membership of the Security Innovation Council are the identical trade associations already lobbying in opposition to right to repair. All of the groups, with the exception of Wiley Rein, are manufacturer trade associations with financial interests in blocking competition for repair. Despite the name, one of them, the Security Industry Association (SIA), represents manufacturers of security cameras, physical locks, and other security devices, not providers of cyber-security software.
Led by Apple and their pronouncement in February 2017 that Nebraska would become a “Mecca for Hackers” by passing repair-friendly legislation, these groups have been hoping to dissuade legislators from moving legislation they do not want through outright fear-mongering. When viewed in this context, the study is as credible as a tobacco industry study of fear of tobacco products.
Factually, hardware repair doesn’t connect with either cyber security or data privacy for very specific and logical reasons. The following diagram shows that hardware security risks are under the control of hardware manufacturers, while software hacking is directed at software, not hardware. Repair of hardware simply does not intersect with documented problems of cyber security.
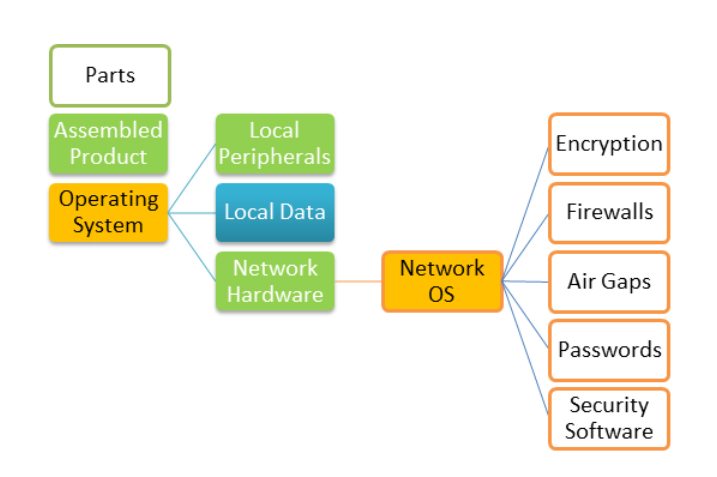
When it comes to hardware security, electronic parts are designed, manufactured and assembled mostly in Asia from a worldwide supply chain. Cyber backdoors can be built into parts at any stage and our national security experts are charged with finding and fixing those flaws. Hardware repair techs cannot create or fix these flaws.
If any of the hardware parts are not working, they must be replaced or the connections restored before any information of any kind can move inside or outside the machine. Repairs must be complete before operating systems or network connections are active. In order for there to be a risk of security from the outside world, products must be actively connected to networks. This is the pivot point at which everything related to security becomes external to hardware and is always related to software.
All interactions between hardware are controlled by some sort of operating system software – either in a full-blown multifunction OS such as Apple IOS or Microsoft Windows, or in a stripped-down mini-OS embedded in the product as “firmware.” It doesn’t matter if the OS is proprietary or open, small or large, simple or complex. Repairs always precede booting up.
The cyber risks are significant if a hacker gets into an operating system, because once inside, they can access anything attached to the OS, including view any locally attached data if it is not encrypted. This is why there is a whole industry of security products protecting access through networks into an operating system. These include firewalls, air gaps and others. Network security hardware itself also requires repair in order to restore functionality when components or connections fail.
Cyber criminals aren’t waiting for legislative permission to dig into insecure networks – they are already getting into poorly secured devices around the world. No one is waiting for a random need for repair in a random location to begin hacking. It is nonsensical to suggest that anyone is trying to access broken equipment that is usually powered down and already inaccessible to networks. Equipment that is down for repair is among the most secure of all because it is offline.
Security experts are widely advocating for more access to firmware specifically for purposes of security research, as documented by filings with the U.S. Copyright Office seeking exemptions for research. These matters are decided by the Copyright Office, further confirming that hardware repair is entirely external to security. The National Institute of Standards and Technology (NIST) has released a draft report to the President on cyber security. Within the report, there is a call for more, not less, transparency on access for research. It is also telling to note that within this 38-page study there is not a single reference to “repair.”
The Repair Association stands willing to discuss credible examples of hardware security issues and how legislation might be recommended to reduce those risks. Recyclers and others in the re-use community can help promote access to information necessary for repair by contacting state legislators anywhere in the US. Go to repair.org/stand-up and fight for your right to re-use.
Gay Gordon-Byrne is the executive director of The Repair Association, a member-led nonprofit umbrella organization of over 240 charities, businesses, trade associations and individuals engaged in repair, reuse, recycling and resale of digital electronic products and services.



